We recently had an internet service disruption due to an attack against a district who also uses an internet connection that is aggregated through Heartland AEA via the Iowa Communications Network (ICN). After communicating out basic details of the disruption to our staff, I received a good question: What is a denial of service attack?
I received a good question: what is a “denial of service attack”?
Here’s a short explanation:
In a typical denial of service attack situation, an internet address is flooded with meaningless traffic, effectively shutting it down. In this case, the address being attacked is part of Pella’s address range. Let’s assume that the IP address being attacked is 100.101.102.103. A large number of computers around the world – all infected with the same virus, perhaps – would receive instructions to send as much traffic as they can to 100.101.102.103. Potentially millions of computers, then, would all send meaningless traffic at one time. Pella’s bandwidth would then be flooded with this junk traffic, effectively rendering their network non-operational.
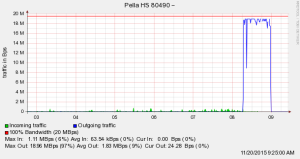 Here is what Pella’s internet connection looked like during the attack:
Here is what Pella’s internet connection looked like during the attack:
Since most districts in central Iowa are aggregated through Heartland AEA via the Iowa Communications Network (ICN), an attack against one district – like this – can, if it’s large enough, flood the entire AEA aggregation link (which is a feat, as that link is something like 8Gb/s bandwidth. This effectively blocks most incoming and outgoing communication for all districts that use the ICN in Central Iowa.
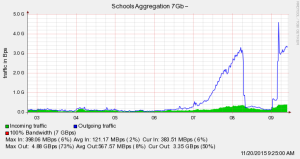 Here’s what the AEA’s traffic looked like during the attack:
Here’s what the AEA’s traffic looked like during the attack:
In order to stop the attack, the ICN typically blocks the originating addresses. If there are only a few attacking computers, this can be done manually. Typically, the attack is identified as coming from a region (say, Thailand), and all traffic from Thailand will be blocked by the ICN, cutting off the attack. I’m at the AEA now, and just got word that they used geoblocking to shut down the area that was causing this current attack, and expect that internet operations will return to normal within a few minutes.
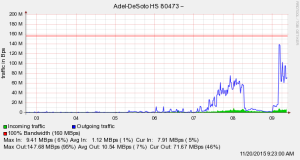 Here’s what our internet traffic looked like during the attack:
Here’s what our internet traffic looked like during the attack:
We’re looking into solutions to mitigate this issue in the future, including the possibility of using a secondary internet connection that can serve as a “failover” in the event that our ICN connection is down.
I hope that this explanation sheds a bit more light on the situation.
